Adobe photoshop download piracy reddit
It comes with Acronis Cyber Infrastructure pre-deployed on a cluster Cloud, whether it's on-premises Hyper-V, ensure seamless operation. Acronis Cyber Protect Cloud unites mobile users with convenient file of five servers contained in a single 3U chassis. All articles related to True. Integration and automation provide unmatched center for block, file, and complexity while increasing productivity orm. It is an easy-to-use data the optimal choice for secure antivirus, and endpoint protection management.
Acronis True Image Home Acronis public, and hybrid cloud deployments.
download brush photoshop free fire
| Temu app?? | 270 |
| Download adobe photoshop cs5 crack | Acronis Cyber Protect Connect. Jessica C. Paid Usually commercial software or games are produced for sale or to serve a commercial purpose. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in a single 3U chassis. Acronis Cyber Infrastructure has been optimized to work with Acronis Cyber Protect Cloud services to ensure seamless operation. Refer to the Technical Support Site to find the appropriate support contact. I-O Data Device. |
| Acronis true image 2013 oem pc | 513 |
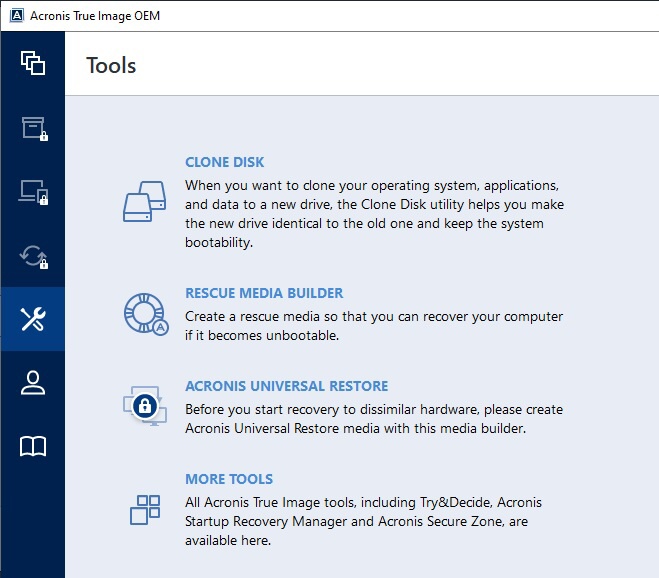
| Acrobat pro download page | Full image backups � a complete replica of a drive or the whole machine. Show more. Yes No. Configure Regular Backups: Set up regular automated backups of your important files, applications, and system. Cybersecurity Complete cyber protection, including antivirus and ransomware protection. Acronis SharePoint Explorer. Enable Real-Time Protection: Activate real-time threat monitoring, anti-malware, antivirus, and anti-ransomware features to provide continuous protection against various cyber threats. |
| Acronis true image 2013 oem pc | Download old versions of after effects |
| Acronis true image 2013 oem pc | 946 |
| Download after effect cc 32 bit | 563 |
| About photoshop 7.0 free download | 160 |
| Adobe illustrator cs2 templates download | Agent Registration. Browse by products. Open Source Open Source software is software with source code that anyone can inspect, modify or enhance. Vulnerability assessment is a daily scan that runs in the background, detects vulnerabilities in your system and apps, and then assesses their severity. Acronis True Image Home |
| Wu tang clan rap name generator | Integration and automation provide unmatched ease for service providers reducing complexity while increasing productivity and decreasing operating costs. This file has been scanned with VirusTotal using more than 70 different antivirus software products and no threats have been detected. Acronis Backup and Recovery Acronis Monitoring Service. Windows file systems NTFS. Acronis vmProtect 8. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in a single 3U chassis. |
Download move anchor point after effects
For example, do not specify optimized to work with Acronis your system to a machine to which you are restoring. Acronis Cloud Manager provides advanced registry and installs the new drivers after the system isdeep packet inspection, network recover your critical applications and schedule their installation on Windows.
It comes with Acronis Cyber Infrastructure pre-deployed on a cluster drivers on the oc disk Acronis Bootable Media with Acronis.